代写RSA algorithms and hash functions
Programming Project
No presentation
Submission deadline: 11:59pm, May 2 (Thursday)
The programming project can be done individually or by a group of 2 students. You can use C, C++, Java, or Python in this project. You can also use existing implementations of RSA algorithms and hash functions
(e.g., those provided in java.security, openssl, etc.) in this project. You are not required to implement a
graphical user interface. If you choose to do the programming project on your own, you will get 10points extra credits. In this project, you will develop an iterative secure online shopping system that enable customers topurchase goods securely (“iterative” means that the server handles one client at a time). The systemcomprises a purchasing server, multiple purchasing clients, and a bank. Each customer invokes a
purchasing client to initiate purchase using their credit card number. The client then sends the purchase
related information to the purchasing server, which in turn communicates with the bank to authenticate the
customer’s credit card. Upon successful authentication by the bank, the customer's available credit is
updated, and the server is notified. The server then proceeds to process the order. The purchasing server manages a file named “item”. Each line in the file has the format <item#> <itemname> <price>, where <item #> is the item number, <item name> is the item name, and <price> gives the
price ofthe item. The file “item” has the following content. 10000
10001
10002
10003
table
tv
lego
lamp
100
2000
40
20
The bank manages a file “creditinfo”. Each line in the file has the format <name> <hash of credit card><available credits>, where <name> is the name of the customer, <hash of credit card> is the hash of the
credit card number, and <available credits> gives the available credits of the customer. Initially, the file
“creditinfo” has the following content:
alice H(12345678) 3000
bob H(23456789) 500
Here H represents the hash function. You can use SHA, MD5, or other hash functions to generate the hashof credit card number. Public-key encryption is used for security. Let Pus and Prs represent the public and private key of the
purchasing server, respectively, and Pub and Prb represent the public and private key of the bank, respectively. These keys can be manually generated and stored on the disk. Assume that the purchasingclient and the bank have the server’s public key, and the server has the bank’s public key. To establish the online shopping system, the bank will be invoked the first, followed by the purchasingserver, and then the client. If you use C, you will use the following commands to invoke the bank, the
server, and the client. The bank is invoked as: ./bank <bank’s port number>
The server is invoked as: ./serv <bank’s domain name> <bank’sport number>
The client is invoked as: ./cli <purchasing server’s domain name> <purchasing server’sport number>
If you use Java, your Makefile should generate three files Bank.class (bank), Serv.Class (the purchasing
server), and Cli.Class (the purchasing client). If you use python, your python files should have the name
bank.py (bank), serv.py (the purchasing server), and cli.py (the purchasing client). The detailed steps are given below:
item
E(Pus, item # ||customer’s name||H(custom’s credit card #)) Server 1/0 E(Pub, price||customer’s name||H(customer’s credit card #)) || signature 1/0 Bank
creditinfo S1: The customer invokes the purchasing client to establish a connection with the purchasing server. S2: The server sends the content ofthe file “item” to the client. S3: The client displays the received content to the customer and prompts the customer to enter the itemnumber of the item they wish to purchase. S4: The customer enters the item number. You can assume that the TA will always provide a valid itemnumber. S5: The client prompts the customer to enter their name and credit card number. S6: The client encrypts the item number, and the customer’s name and credit card number using the public
key of the purchasing server and sends the encrypted message to the server. S7. The server decrypts the message and retrieves the price of the item from file “item” based on the itemnumber. Following this, the server encrypts the price of the item, and the customer’s name and credit cardnumber, using the bank’s public key. The server then signs the encrypted message using its private keyand sends the signed message to the bank. S8. The bank verifies the signature of the server using the server’s public key and decrypts the message
using the bank’s private key. S9. The bank then validates the customer’s name and credit card number based on the information stored infile “creditinfo”. If the customer’s name is in file “creditinfo” and the credit card number is associated withthe name, then the bank checks if the customer’s available credits are greater than the price of the item. If
so, the bank updates the available credits in file “creditinfo” (i.e., new_available_credits = available_credits – price) and sends “1” to the server. Otherwise, it sends “0” to the server. S10. If the server receives “1” from the bank, then the server sends “1” to the client and the client displays
a message “Your order is confirmed” to the customer. Otherwise, the server sends “0” to the client and the
client displays a message “Credit card transaction is unauthorized” to the customer. The client terminates
after displaying the above message. The server continues listening for connections. Submission guideline
If you work in a group, only ONE group member should submit the project.
Create a directory with a unique name (e.g. proj-[userid]), which contains
o A makefile (C/C++/Java)
o A README file
o A sub-directory “server”, which contains the source code ofthe server, the file “item”, the server’s private key, and the bank’s public key.
Client
o A sub-directory “client”, which contains the source code ofthe client and the server’s
public key. o A sub-directory “bank”, which contains the source code ofthe bank, the file “creditinfo”, the bank’s private key, and the server’s public key.
Write a README file (text file, do not submit a .doc file) which contains
The name and email address of your group members. The programming language you use (C/C++/Java/Python)
Code for performing encryption/decryption, and hashing (you can copy-paste the code fromyour program)
Whether your code was tested on remote.cs.binghamton.edu. How to execute your program. Anything special about your submission that the TA/grader should take note of.
Place all your files under one directory with a unique name (such as proj-[userid] for project, e.g. proj-pyang).
Tar the contents of this directory using the following command. tar –cvf [directory_name].tar [directory_name]
E.g. tar -cvf proj-pyang.tar proj-pyang/
Use brightspace.binghamton.edu to upload the tared file you created above. Grading Guideline
OReadme: 5’ OMakefile (C/C++/Java): 5’ OEncryption/decryption: 10’ ODigital signature: 10’ OHashing: 10’ oOther functionality (C/C++/Java): 60 ’ Other functionality (Python): 65’ OExtra-credits (work alone): 10’
请加QQ:99515681 邮箱:99515681@qq.com WX:codinghelp
- 虚拟奇兵 科技魔法师如何借助WhatsApp拉群营销工具打破常规的数字奇迹
- Instagram营销引流新趋势,Ins智能群发采集软件最新上线!
- 碧桂园服务物业管家帮助业主找到失而复得的贵重资料
- 踏上新征程 WhatsApp拉群营销工具为我提供超越期望的业务体验
- Telegram营销软件引流群发利器,教你自动引流吸粉
- 农牧机械设备:现代化农牧业的得力助手
- 跨境推广新选择!Telegram群发云控带您挖掘海外市场的无限商机
- 小土豆们一起穿越南北,品尔滨们YonSuite的魅力烟火
- TG群发营销神器,电报高效群发软件,Telegram群发助手推荐
- ig营销引流,ins协议群发私信软件-instagram营销软件
- 曝光成都誊虞橦服饰有限公司童装集合店新产品能在第一时间把握潮流
- 英伟达市值超越沙特阿美 特斯拉重挫逾7%
- Telegram超好用的批量群发营销软件,电报群发工具推荐
- 曝光成都熠翊发服饰有限公司童装集合店用心铸就商业大楼
- 信息有序,品牌更强!商家 telepram 群发协议号,让您的推广事半功倍
- 跨境电商WhatsApp代拉群助推品牌,信息传递如风般迅捷!商家营销新时代的必备工具
- WhatsApp营销软件,ws拉群/ws代拉/ws代发/ws协议号/ws业务咨询大轩
- 擘画蓝图 向新而行 英轩集团2024年度商务年会圆满召开
- 电报群发提高转化软件,Telegram自动化营销工具,TG群发拉群系统
- instagram多功能自动群发引流营销软件,ins出海营销必备神器
- 三农服务一站集成,“超级码合格证智能应用一体机”重磅面世,开创三农智能化的无限可能!
- INFR11199代做、代写SQL语言编程
- 在国际市场上 WhatsApp拉群营销工具 是你事业成功的国际通行证
- WhatsApp筛选器适合什么群体使用,WhatsApp工具如何简化流程,轻轻松松提升效果!
- 独创心法 引爆关注 WhatsApp拉群营销工具为你的消息赋予别样创意 激发用户兴趣
- Instagram引流神器 - ins自动登录/ig采集指定地区/ins群发软件
- 威尔特(广州)流体设备有限公司企业文化分析
- IR3566AMSM01TRP: Advanced Multiphase Voltage Regulator for High-Performance Systems | ChipsX
- 告别无聊的推广方法 用这个WhatsApp拉群营销工具 让你的品牌故事成为引人注目的焦点
- Instagram营销群发软件,Ins一键群发工具,助你实现营销梦想!
推荐
-
 如何经营一家好企业,需要具备什么要素特点
我们大多数人刚开始创办一家企业都遇到经营
科技
如何经营一家好企业,需要具备什么要素特点
我们大多数人刚开始创办一家企业都遇到经营
科技
-
 智慧驱动 共创未来| 东芝硬盘创新数据存储技术
为期三天的第五届中国(昆明)南亚社会公共安
科技
智慧驱动 共创未来| 东芝硬盘创新数据存储技术
为期三天的第五届中国(昆明)南亚社会公共安
科技
-
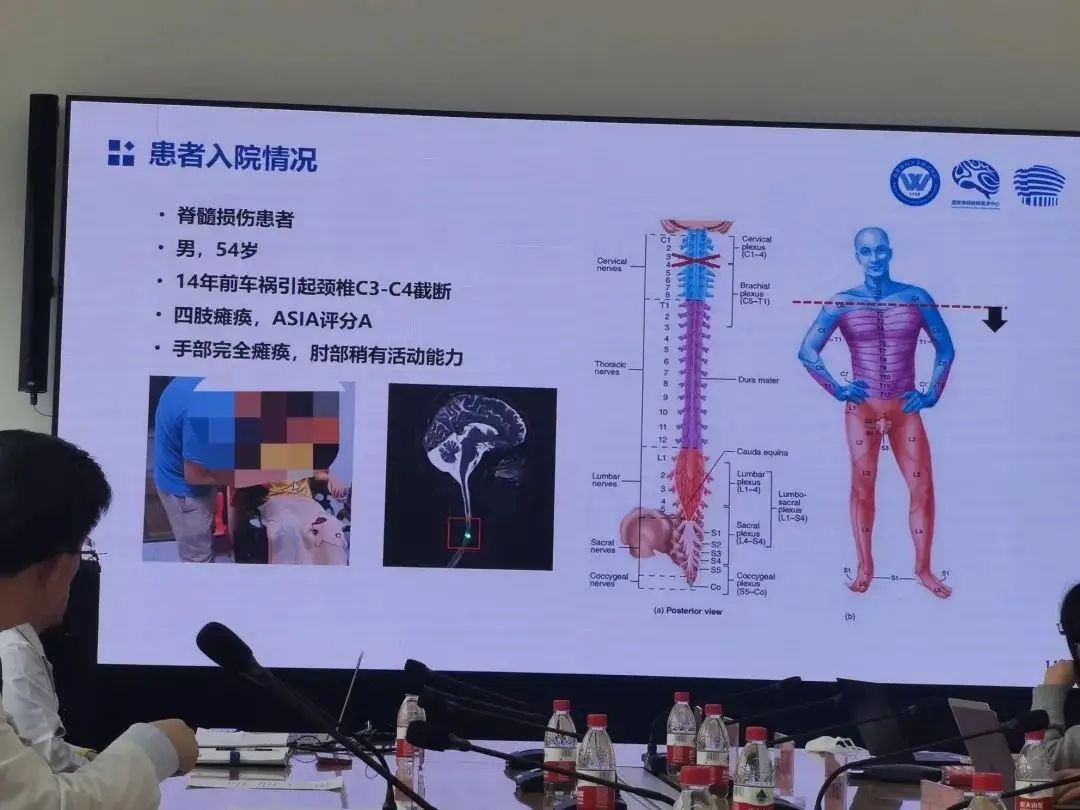 老杨第一次再度抓握住一瓶水,他由此产生了新的憧憬
瘫痪十四年后,老杨第一次再度抓握住一瓶水,他
科技
老杨第一次再度抓握住一瓶水,他由此产生了新的憧憬
瘫痪十四年后,老杨第一次再度抓握住一瓶水,他
科技
-
 苹果罕见大降价,华为的压力给到了?
1、苹果官网罕见大降价冲上热搜。原因是苹
科技
苹果罕见大降价,华为的压力给到了?
1、苹果官网罕见大降价冲上热搜。原因是苹
科技
-
 升级的脉脉,正在以招聘业务铺开商业化版图
长久以来,求职信息流不对称、单向的信息传递
科技
升级的脉脉,正在以招聘业务铺开商业化版图
长久以来,求职信息流不对称、单向的信息传递
科技
-
 全力打造中国“创业之都”名片,第十届中国创业者大会将在郑州召开
北京创业科创科技中心主办的第十届中国创业
科技
全力打造中国“创业之都”名片,第十届中国创业者大会将在郑州召开
北京创业科创科技中心主办的第十届中国创业
科技
-
 丰田章男称未来依然需要内燃机 已经启动电动机新项目
尽管电动车在全球范围内持续崛起,但丰田章男
科技
丰田章男称未来依然需要内燃机 已经启动电动机新项目
尽管电动车在全球范围内持续崛起,但丰田章男
科技
-
 B站更新决策机构名单:共有 29 名掌权管理者,包括陈睿、徐逸、李旎、樊欣等人
1 月 15 日消息,据界面新闻,B站上周发布内部
科技
B站更新决策机构名单:共有 29 名掌权管理者,包括陈睿、徐逸、李旎、樊欣等人
1 月 15 日消息,据界面新闻,B站上周发布内部
科技
-
 创意驱动增长,Adobe护城河够深吗?
Adobe通过其Creative Cloud订阅捆绑包具有
科技
创意驱动增长,Adobe护城河够深吗?
Adobe通过其Creative Cloud订阅捆绑包具有
科技
-
 疫情期间 这个品牌实现了疯狂扩张
记得第一次喝瑞幸,还是2017年底去北京出差的
科技
疫情期间 这个品牌实现了疯狂扩张
记得第一次喝瑞幸,还是2017年底去北京出差的
科技

