COMP1212代写、代做Java/c++程序设计
School of Computing: assessment brief
Module title Computer Processors
Module code COMP1212
Assignment title Assignment 2: Encryption using a Feistel Cipher
Assignment type
and description
In-course assessment. Requires design, implementation
and testing of code written in assembly language
Rationale
Provides an opportunity to write assembly code including
understanding the implementation of branching and
functions and learn how a Feistel Cipher works for encryption.
Word
limit and
guidance
This coursework should take less than 15 hours to complete.
Weighting
60%
Submission deadline
10am
9/5/24
Submission
method
Gradescope
Feedback provision Feedback will be provided through Gradescope
Learning outcomes
assessed
Explain how high level programming constructs, such
as ’if’ statements and ’for’ loops, are implemented at a
machine level
Module lead Andy Bulpitt
Other Staff contact Noleen K¨ohler
11. Assignment guidance
The Feistel cipher is a symmetric block cipher encryption framework which is the basis
of many modern day encryption algorithms. In this coursework you will implement
a Feistel cipher system as a software implementation in Hack Assembly.
In a Feistel cipher the plaintext, P, to be encrypted is split into two equal size parts
L0 and R0 such that P = L0R0. A function F is applied to one half of the plaintext,
combined with a key, and the result is XOR’d with the other half of the plaintext.
Feistel ciphers often employ multiple rounds of this scheme. In general the scheme
works as follows, for all i = 0, . . . , n,
Li+1 = Ri
Ri+1 = Li ⊕ F(Ri
, Ki)
To decrypt an encrypted message using this cipher we can apply the same procedure
in reverse. For i = n, n − 1, . . . , 0,
Ri = Li+1
Li = Ri+1 ⊕ F(Li+1, Ki)
For this coursework we are interested in the 16-bit Feistel cipher which uses 4 rounds.
The function F(A, B) = A ⊕ ¬B.
The keys are derived from a single 8-bit key K0 such that,
K0 = b7b6b5b4b3b2b1b0
K1 = b6b5b4b3b2b1b0b7
K2 = b5b4b3b2b1b0b7b6
K3 = b4b3b2b1b0b7b6b5
2. Assessment tasks
(a) Write a program (XOR.asm) in HACK assembly that implements a bit-wise
XOR function between two 16-bit values stored in RAM[3] and RAM[4] and
stores the result in RAM[5].
[4 marks]
2(b) Write a program (Rotate.asm) in HACK assembly that implements an algorithm
to rotate the bits of a 16-bit number left (Least Significant bit (LSb) to Most
Significant bit (MSb)). The original number should be stored in RAM[3], the
number of times to rotate the bits should be in RAM[4] and the result stored in
RAM[5], i.e. 1010111100000000 rotated left 3 times would be 0111100000000101
where the MSb is used to replace the LSb on each rotation.
[8 marks]
(c) Write a program (FeistelEncryption.asm) in HACK assembly, that implements
the described Feistel encryption system. The initial key, K0, will be stored in
RAM[1], and the plaintext to be encrypted will be represented by a 16-bit value
stored in RAM[2]. The result of the encryption should be stored in RAM[0].
[10 marks]
[Total 22 marks]
3. General guidance and study support
Tools required to simulate the hardware and CPU are provided on Minerva under
Learning resources: Software. You may find it easier to implement cipher in a high
level language first. This will also allow you to test the results of your HACK program.
Support will be available during lab classes. Please ensure the files you upload work
with the test files provided and use the filenames provided in this sheet. Do not
alter the format of the lines of these test files in any way. The spacing in
each line needs to be preserved You are of course welcome to build your own
test files in the same format or add to these files.
4. Assessment criteria and marking process
This coursework will be automatically marked using Gradescope. Feedback will be
provided through Gradescope.
Marks are awarded for passing the automated tests on the submitted programs.
These will not necessarily be the same tests that are provided to help you develop
the solution. You should therefore test your solution thoroughly using other values
for the plaintext and keys before your final submission.
5. Presentation and referencing
Submitted code should provide suitable comments where possible.
6. Submission requirements
Links to submit your work can be found on Minerva under Assessment and feedback/Submit
my work. The HACK assembly (asm) files for each part must be uploaded
individually. Ensure you use only the filenames provided in this specification
sheet.
37. Academic misconduct and plagiarism
Academic integrity means engaging in good academic practice. This involves essential
academic skills, such as keeping track of where you find ideas and information and
referencing these accurately in your work.
By submitting this assignment you are confirming that the work is a true expression
of your own work and ideas and that you have given credit to others where their
work has contributed to yours.
8. Assessment/marking criteria
No marks will be awarded for tests which fail
• Part a) is graded using 4 tests, each worth 1 mark. [max 4 marks]
• Part b) is graded using 4 tests, each worth 2 marks. [max 8 marks]
• Part c) is graded using 4 tests, each worth 2 marks and a further 2 marks for
optimised solutions that require a lower number of operations to complete the
encryption [max 10 marks]
[Total 22 marks]
4
请加QQ:99515681 邮箱:99515681@qq.com WX:codinghelp
- COMP30024代写、Playing the Game代做
- 深圳科华荣获2024“北极星杯”两项行业大奖!
- WhatsApp营销软件/ws群发/ws协议号/ws筛选/ws接粉
- Telegram群发工具,轻松引流!营销效果倍增!
- 精细化数据工艺:Line代筛料子专业团队为您打造一手数据精品
- Ig营销引流攻略,Instagram2024最强群发工具推荐,ins引流秘籍
- EIG 旗下 MidOcean Energy 将收购 SK Earthon 在秘鲁液化天然气(PLNG)公司 20% 的股份
- 聊城物流网:连接世界的物流枢纽,助力城市腾飞
- 科技感官奇兵,WhatsApp拉群工具
- CIT 594代做、代写Python设计编程
- 电报群发软件推荐,Telegram自动采集群发工具/TG协议号购买
- 便捷Line代群发,助您迅速提升用户互动!
- Instagram引流软件,Ins一键自动增粉,打破爆粉秘籍!
- 北京爱尔新力眼科:45岁患者选择摘镜手术 做更好的自己
- 宁夏构建西部医疗健康行业大模型生态,引领医疗创新与数字化转型
- 贵州装饰网:引领装饰新风尚,缔造家居美学新境界
- 新点软件参编的《工程建设项目与建筑市场数据标准》正式发布
- 低成本引流推广!Ins自动私信工具,Instagram营销软件推荐!
- Telegram营销软件引流群发利器,教你自动引流吸粉
- XC2V3000-4FGG676I: Advancing High-Performance Computing with FPGA Excellence | ChipsX
- instagram2024年最强群发营销软件来袭!ins自动推广引流利器
- instagram群发采集神器,高效引流爆粉,助你成为社交达人!
- Instagram营销软件,ins定位采集工具/采集全球任意国家
- 开启零售业的未来:2024 年非洲数字零售会议
- 代做Air Quality in New York City
- instagram自动引流新招,ins一键打粉推广软件推荐
- ws/WhatsApp营销软件,ws协议号群发优化/ws拉群自动化/ws劫持号详情
- Instagram怎么快速引流获客,ins群发营销软件,ig引流工具推荐
- 明牌珠宝——刘涛春日新形象,中国浪漫,蝶恋花开
- CSC1002代写、代做Python/c++语言程序
推荐
-
 如何经营一家好企业,需要具备什么要素特点
我们大多数人刚开始创办一家企业都遇到经营
科技
如何经营一家好企业,需要具备什么要素特点
我们大多数人刚开始创办一家企业都遇到经营
科技
-
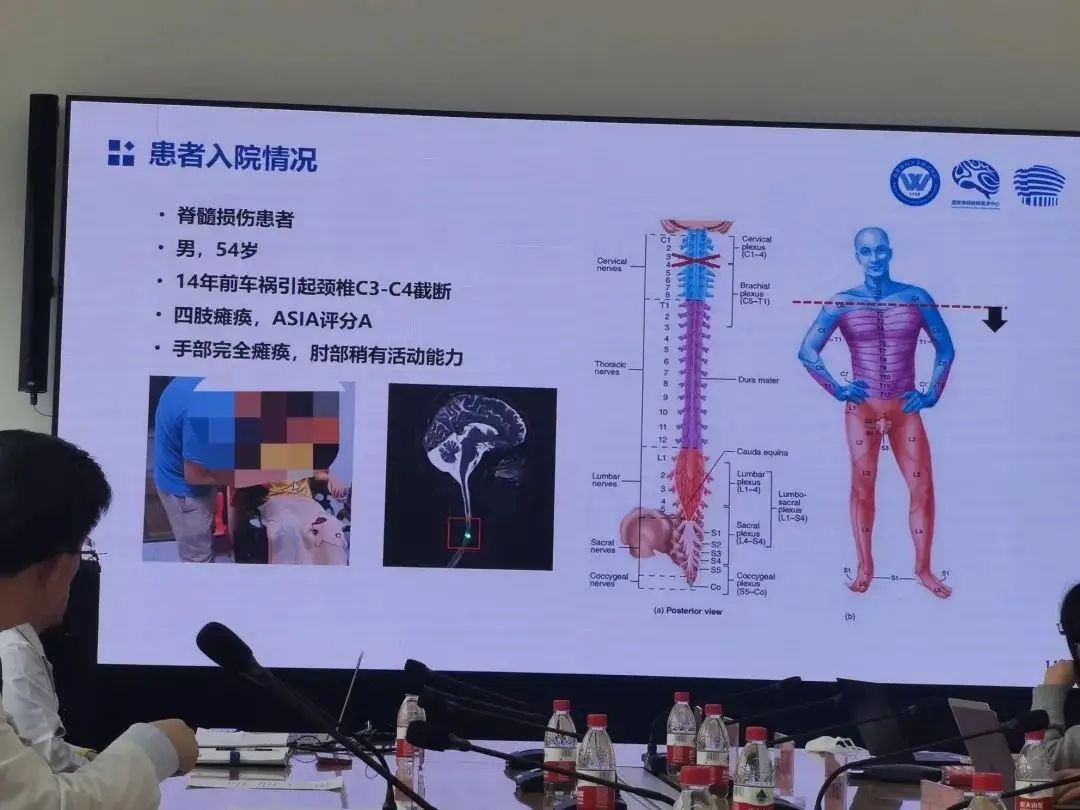 老杨第一次再度抓握住一瓶水,他由此产生了新的憧憬
瘫痪十四年后,老杨第一次再度抓握住一瓶水,他
科技
老杨第一次再度抓握住一瓶水,他由此产生了新的憧憬
瘫痪十四年后,老杨第一次再度抓握住一瓶水,他
科技
-
 B站更新决策机构名单:共有 29 名掌权管理者,包括陈睿、徐逸、李旎、樊欣等人
1 月 15 日消息,据界面新闻,B站上周发布内部
科技
B站更新决策机构名单:共有 29 名掌权管理者,包括陈睿、徐逸、李旎、樊欣等人
1 月 15 日消息,据界面新闻,B站上周发布内部
科技
-
 升级的脉脉,正在以招聘业务铺开商业化版图
长久以来,求职信息流不对称、单向的信息传递
科技
升级的脉脉,正在以招聘业务铺开商业化版图
长久以来,求职信息流不对称、单向的信息传递
科技
-
 苹果罕见大降价,华为的压力给到了?
1、苹果官网罕见大降价冲上热搜。原因是苹
科技
苹果罕见大降价,华为的压力给到了?
1、苹果官网罕见大降价冲上热搜。原因是苹
科技
-
 全力打造中国“创业之都”名片,第十届中国创业者大会将在郑州召开
北京创业科创科技中心主办的第十届中国创业
科技
全力打造中国“创业之都”名片,第十届中国创业者大会将在郑州召开
北京创业科创科技中心主办的第十届中国创业
科技
-
 丰田章男称未来依然需要内燃机 已经启动电动机新项目
尽管电动车在全球范围内持续崛起,但丰田章男
科技
丰田章男称未来依然需要内燃机 已经启动电动机新项目
尽管电动车在全球范围内持续崛起,但丰田章男
科技
-
 疫情期间 这个品牌实现了疯狂扩张
记得第一次喝瑞幸,还是2017年底去北京出差的
科技
疫情期间 这个品牌实现了疯狂扩张
记得第一次喝瑞幸,还是2017年底去北京出差的
科技
-
 智慧驱动 共创未来| 东芝硬盘创新数据存储技术
为期三天的第五届中国(昆明)南亚社会公共安
科技
智慧驱动 共创未来| 东芝硬盘创新数据存储技术
为期三天的第五届中国(昆明)南亚社会公共安
科技
-
 创意驱动增长,Adobe护城河够深吗?
Adobe通过其Creative Cloud订阅捆绑包具有
科技
创意驱动增长,Adobe护城河够深吗?
Adobe通过其Creative Cloud订阅捆绑包具有
科技

