COMP3334代做、代写Python程序语言
COMP3334 Project
End-to-end encrypted chat web application
Semester 2, 2023/2024
Nowadays, web services are the most
common form of applications that users are
exposed to. Web browsers become the most
popular application on a computer that
enables users to access those web services.
Ensuring the security of web services is
essential for the Internet. Moreover, privacy
of communications is an important feature of
modern times. Your job is to implement an
end-to-end encrypted chat web application
and secure various aspects of the website.
Overview
Objectives
1. Adapt a basic chat web application to become a secure E2EE chat web app
2. Comply with some of the requirements in NIST Special Publication 800-63B “Digital
Identity Guidelines – Authentication and Lifecycle Management” for US federal
agencies (which is also a reference for other types of systems)
3. Implement a secure MFA mechanism based on passwords and OTP (or FIDO2)
4. Encrypt communications between two users so that the server does not know the
content of the messages (E2E encryption)
5. Protect communications in transit by configuring a modern TLS deployment
6. Package a docker image of your web app
Requirements (authentication)
1. From NIST Special Publication 800-63B:
1. Comply with all SHALL and SHOULD requirements from sections listed below
2. Use the following authenticators:
• User-chosen Memorized Secret (i.e., password/passphrase)
• and Single-Factor OTP Device (e.g., Google Authenticator)
• or Single-Factor Cryptographic Device (e.g., Yubikey) if you have one
• and Look-Up Secrets (recovery keys)
• Comply with related requirements in §5.1 and §4.2.2
• §5.1.1.2: “Memorized secrets SHALL be salted and hashed using a suitable one-way key
derivation function”
• See our Password Security lecture for an appropriate function
• Memorized Secret Verifiers (§5.1.1.2)
• Choose “Passwords obtained from previous breach corpuses” and refer to
https://haveibeenpwned.com/API/v3#PwnedPasswords for the corpus to check against
• §5.2.8 and §5.2.9 are automatically complied
Requirements (authentication)
1. From NIST Special Publication 800-63B:
3. §5.2.2: Implement rate-limiting mechanisms AND image-based CAPTCHAs
4. Implement new account registration and bind authenticators (OTP/Yubikey and recovery keys) at
the same time
• Optional: provide a way to change authenticators after account registration
5. §7.1: Implement proper session binding requirements
6. Exceptions:
• OTP authenticators — particularly software-based OTP generators — SHOULD discourage and
SHALL NOT facilitate the cloning of the secret key onto multiple devices.
• Google Authenticator and related apps are OK
Requirements (E2EE chat)
2. Once users are logged in, secure chat messages between two users in a way so that the server cannot
decrypt the messages
1. Use the ECDH key exchange protocol to establish a shared secret between two users
• Leverage the WebCrypto API, see demo https://webkit.org/demos/webcrypto/ecdh.html
• Exchanged information during the key exchange can be sent through the server
• The server is trusted not to modify messages of the key exchange
• Choose P-384 as the underlying curve
2. Derive two 256-bit AES-GCM encryption keys and two 256-bit MAC keys from the shared secret
using HKDF-SHA256
• One key for encryption between user1 to user2, and another one from user2 to user1
• Using WebCrypto API again, see https://developer.mozilla.org/enUS/docs/Web/API/HkdfParams
• The salt should be unique so another key derivation in the future produces different keys, use
for instance a counter starting at 1
• The info parameter should represent the current context (e.g., “CHAT_KEY_USER1to2” for the
key for user1user2, and “CHAT_MAC_USER1to2” for the MAC key for user1user2)
Requirements (E2EE chat)
2. Once users are logged in, secure chat messages between two users in a way so that the server cannot
decrypt the messages
3. Messages will be encrypted using AES in GCM mode
• 96-bit IVs are counters representing the number of messages encrypted with the same key
• Note: GCM does not require unpredictable IVs, but unique IVs
• Send the IV together with the ciphertext to the recipient
• As a recipient, verify that IV
- 全新网络通信标识推广方案,Line协议号注册器助您一站式解决!
- 新质生产力发展划重点,第十二届上海国际泵阀展预登记“福”力全开!
- Telegram引流利器,智能群发采集,助你快速引流!
- Ins批量筛选群发营销采集神器,Instagram营销工具,助你轻松营销!
- 郑州大学第一附属医院:构建智能化报告系统平台,加速个体化用药时代到来
- ins拉群软件,ins群发软件,ins营销软件联系天宇爆粉【TG:@cjhshk199937】
- instagram最靠谱群发引流营销软件,ins最强自动采集粉丝工具
- 英伟达市值超越沙特阿美 特斯拉重挫逾7%
- 构建GIS网络安全体系 赋能自然资源数字化治理能力提升
- Ins/Instagram精准引流软件,ins群发营销打粉新高度!
- 威尔特(广州)流体 - MR V服务体系分析
- instagram群发引流大师,高效采集用户,助你轻松爆粉!
- 数字经济时代,环保水务科技产业十大战略技术趋势
- 预祝华晨禾一开业启动暨客户交流会圆满召开!
- 国家重点研发计划“主动健康”专项课题终期验收会召开,神州医疗承担课题顺利通过验收
- 四川速冻平台:让美食瞬间锁鲜,轻松品味四川风味
- Telegram一键批量私信营销软件,每条发送上万条消息!
- ins群发营销软件,instagram营销软件,天宇爆粉【TG:@cjhshk199937】
- 《智慧城市“一网统管”运营研究报告2024》发布,新点软件参编助力
- 星际商海的新星探:2024年是否有跨境电商 Telegram 群发云控冒险者成为星际商海的新星探,勘探新商机
- instagram群发引流必备,高效采集用户,助你实现社交爆粉!
- 埃塞俄比亚#Telegram协议号-telegram劫持号-telepram拉群软件自产自销量大价稳
- Ins爆粉机器人,Instagram引流营销软件全球震撼推荐!
- 宗庆后40条经典语录,给企业家的宝贵财富!
- 《热辣滚烫》掀起健康减脂潮流,植物基食品迎来“第二春”?
- 在没有LINE工具的日子里,我的业务就像是一朵不开花的枯草
- 不知道如何在WhatsApp拉群上引爆品牌 这个工具一键解决你的烦恼 品牌传播无压力
- 2024泰普尔新春发布会启航“泰”空征程,焕新睡眠科技震撼登场
- x增长的秘诀:LINE工具,数字化引擎的无敌之选!
- 成功博主心语 WhatsApp拉群营销工具的引发好奇 业务成果直逼巅峰
推荐
-
 创意驱动增长,Adobe护城河够深吗?
Adobe通过其Creative Cloud订阅捆绑包具有
科技
创意驱动增长,Adobe护城河够深吗?
Adobe通过其Creative Cloud订阅捆绑包具有
科技
-
 全力打造中国“创业之都”名片,第十届中国创业者大会将在郑州召开
北京创业科创科技中心主办的第十届中国创业
科技
全力打造中国“创业之都”名片,第十届中国创业者大会将在郑州召开
北京创业科创科技中心主办的第十届中国创业
科技
-
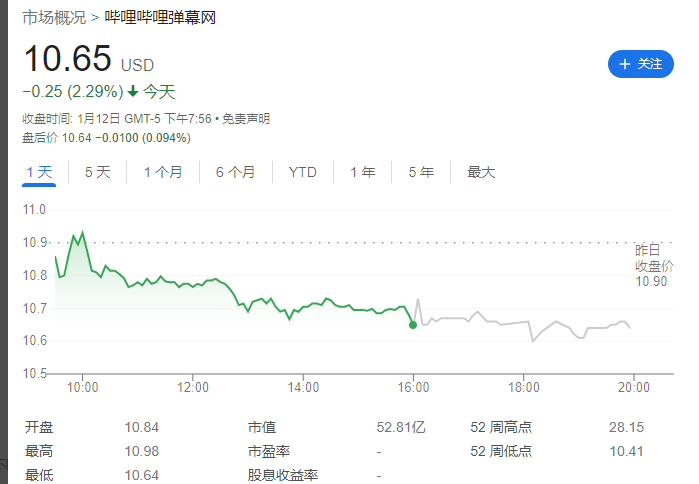 B站更新决策机构名单:共有 29 名掌权管理者,包括陈睿、徐逸、李旎、樊欣等人
1 月 15 日消息,据界面新闻,B站上周发布内部
科技
B站更新决策机构名单:共有 29 名掌权管理者,包括陈睿、徐逸、李旎、樊欣等人
1 月 15 日消息,据界面新闻,B站上周发布内部
科技
-
 如何经营一家好企业,需要具备什么要素特点
我们大多数人刚开始创办一家企业都遇到经营
科技
如何经营一家好企业,需要具备什么要素特点
我们大多数人刚开始创办一家企业都遇到经营
科技
-
 苹果罕见大降价,华为的压力给到了?
1、苹果官网罕见大降价冲上热搜。原因是苹
科技
苹果罕见大降价,华为的压力给到了?
1、苹果官网罕见大降价冲上热搜。原因是苹
科技
-
 升级的脉脉,正在以招聘业务铺开商业化版图
长久以来,求职信息流不对称、单向的信息传递
科技
升级的脉脉,正在以招聘业务铺开商业化版图
长久以来,求职信息流不对称、单向的信息传递
科技
-
 疫情期间 这个品牌实现了疯狂扩张
记得第一次喝瑞幸,还是2017年底去北京出差的
科技
疫情期间 这个品牌实现了疯狂扩张
记得第一次喝瑞幸,还是2017年底去北京出差的
科技
-
 丰田章男称未来依然需要内燃机 已经启动电动机新项目
尽管电动车在全球范围内持续崛起,但丰田章男
科技
丰田章男称未来依然需要内燃机 已经启动电动机新项目
尽管电动车在全球范围内持续崛起,但丰田章男
科技
-
 智慧驱动 共创未来| 东芝硬盘创新数据存储技术
为期三天的第五届中国(昆明)南亚社会公共安
科技
智慧驱动 共创未来| 东芝硬盘创新数据存储技术
为期三天的第五届中国(昆明)南亚社会公共安
科技
-
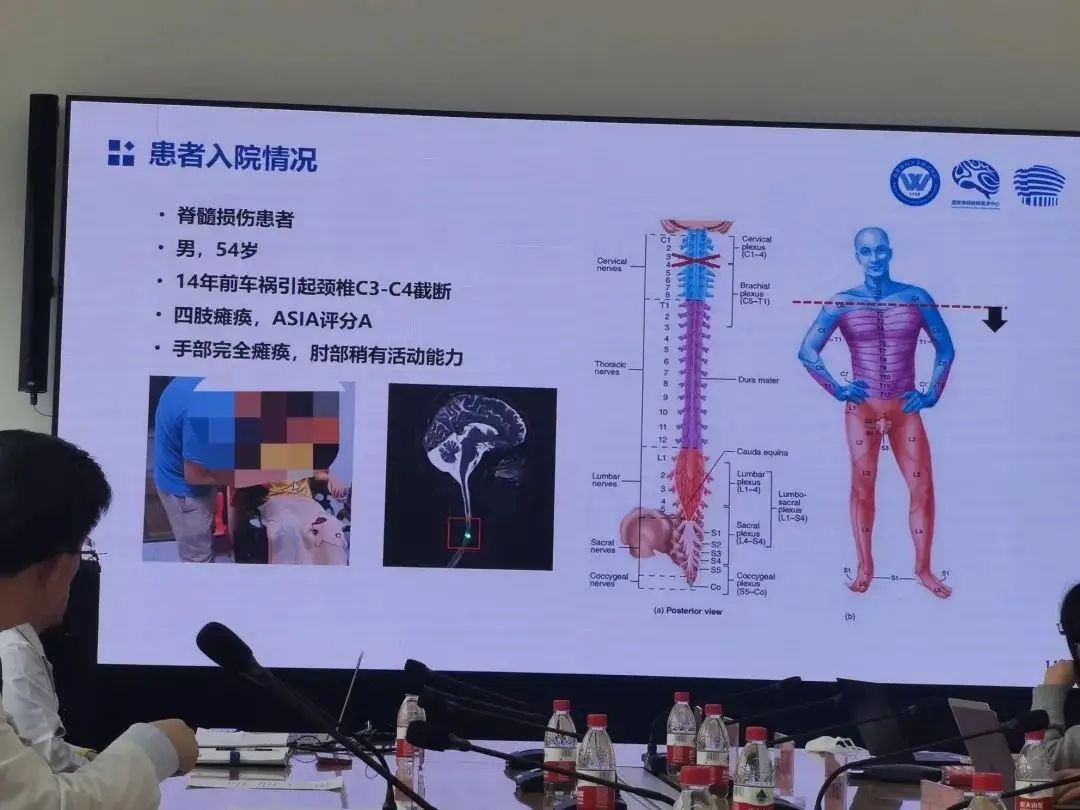 老杨第一次再度抓握住一瓶水,他由此产生了新的憧憬
瘫痪十四年后,老杨第一次再度抓握住一瓶水,他
科技
老杨第一次再度抓握住一瓶水,他由此产生了新的憧憬
瘫痪十四年后,老杨第一次再度抓握住一瓶水,他
科技

