CHC5223代做、java语言编程代写
CHC5223 Data Structures and Algorithms 2023–2024 Semester 2
1 of 4
Assignment 1
Value 40% of Coursework
Individual work
Learning outcomes
Students will be able to understand:
1.1 Data structures
1.2 The applications of data structures
1.3 Object-oriented programming concepts
1.4 Methods for program testing
Students will have acquired skills in:
2.1 Data abstraction
2.2 The use of data structures
2.3 Programming at a more advanced level in a high-level object-oriented language
2.4 Program testing and documentation
Students will have acquired skills in:
3.1 Self-management
3.2 Learning
3.3 Communication
3.4 Problem solving
3.5 Information technology
Submission requirements
The assignment submitted should be compressed into a .zip file, the following files should be
contained in the compressed file:
• a report as a Microsoft Word document containing the code of all your classes.
filename format: student ID+CHC5223_CW1_Report.docx
• a .zip file containing the project: the runnable jar file (if available) and all the program’s
source code (.java).
filename format: student ID+CHC5223_ CW1_Files.zip
General requirements
All your programming must conform to “Java Conventions and Programming Guidelines” – see
module Moodle site.
You must paste the key source code of your implementation into your report, as text or as
screenshots.
Introduction
The topics of this assignment are array, linked list, and hash table. The objective of this
assignment is to develop a hash table data structure utilizing a double-linked list as the
underlying mechanism.
Requirements
Basic rules
You must create one executable project after completing all tasks.
One Java class should be defined in one .java file respectively.
CHC5223 Data Structures and Algorithms 2023–2024 Semester 2
2 of 4
In the report, the source code of each task, together with the corresponding explanation, should
be presented separately.
Failure to comply with these rules will result in zero marks.
Task 1
You must design and implement a doubly linked list without using any existing implementation
in Java.
➢ The double-linked list should be a generic data structure that can store elements of string
data type.
➢ You must create a Node class that represents each element in the doubled-linked list.
➢ You must create a LinkedList class that represents a doubly linked list which should include
methods for inserting, deleting, accessing specific elements, checking empty, returning size,
and other operations you want to implement.
➢ The insertion operation should be done at the front of the list.
➢ The implementation should include error handling to handle errors such as deleting
elements from an empty list and accessing out-of-bounds.
5 marks
You must give clear rationales and detailed explanations of your design and implementation in
the report.
5 marks
Task 2
You must design and implement a hash table based on a Java array (not any array list or existing
implementation from the Java library) and achieve the collision solution by using the linear
probing way.
➢ You must create a LinearProbingHashTable class that represents a hash table by using the
linear probing way for collision resolution. The initial capacity of the array should not
exceed 20.
➢ You must devise a hash function that can work well for string-type data. The hash function
devised should minimize the occurrence of collisions. You must not use the Java built-in
hashCode method, though you can experiment with it.
➢ The implementation can handle errors such as null keys or keys with unexpected formats.
➢ The implementation should include methods for inserting, searching, deleting, and
accessing key-value pairs.
➢ The implementation of the inserting operation can resize the table efficiently according to
the strategy you design if the hash table is too full.
➢ The implementation of the deleting operation can handle the situation when the key is not
found.
➢ The implementation can keep track of the load factor of the hash table and display it after
each insertion or deletion.
➢ The implementation of the searching operation can search for the key and return the
corresponding value if the key is found.
5 marks
You must give clear rationales and detailed explanations of your design and implementation in
the report.
CHC5223 Data Structures and Algorithms 2023–2024 Semester 2
3 of 4
5 marks
Task 3
You must design and implement a hash table based on the linked list and achieve the collision
solution by using the separate chaining way.
➢ You must create a ChainingHashTable class that represents a hash table by using the
separate chaining way for collision resolution.
➢ You must use the doubly linked list devised in task 1 to implement the separate chaining
way. The capacity of the linked list of separate chaining should not exceed 8.
➢ You must devise a hash function that can work well for string-type data. The hashing
strategy of the hash function should be designed differently from that of task 2 and should
minimize the occurrence of collisions. You must not use the Java built-in hashCode method,
though you can experiment with it.
➢ The implementation can handle errors such as null keys or keys with unexpected formats.
➢ The implementation should include methods for inserting, searching, deleting, and
accessing key-value pairs, as well as determining load factor.
➢ The implementation of the inserting operation can resize the table efficiently if the hash
table is too full.
➢ The implementation of the deleting operation can handle the situation when the key is not
found.
➢ The implementation can keep track of the load factor of the hash table and display it after
each insertion or deletion.
➢ The implementation of the searching operation can search for the key and return the
corresponding value if the key is found.
➢ The implementation of the hash table can resize the table capacity according to the
strategy you designed.
5 marks
You must give clear rationales and detailed explanations of your design and implementation in
the report.
5 marks
Task 4
You must implement a main program that engages objects of both the LinearProbingHashTable
class and the ChainingHashTable class.
➢ You must design a set of test cases to evaluate the functionality and correctness of two
different hash tables.
• Set the capacity of the hash table to a small value so that collisions are easy to occur.
• Verify that each of the hash functions is working well.
• Verify that each of the implemented methods is working correctly.
• Verify that the implementations of the Linear Probing way and Separate Chaining way
for collision solutions are working effectively.
➢ The inner structure of the generated hash tables should be clearly illustrated as the
executed result of the program.
4 marks
CHC5223 Data Structures and Algorithms 2023–2024 Semester 2
4 of 4
You must give clear rationales and detailed explanations of your design and implementation in
the report.
➢ Demonstrate the executed result of the program, including the generated hash table and
corresponding test data.
➢ Contrast and analyze the two hash tables generated based on the same set of test cases
given.
➢ Contrast and analyze the difference between the two hash functions you devised based on
the same set of test cases given.
➢ Give a rationale and detailed analysis of the effects of two different strategies of collision
solution.
6 marks
total 40 marks
Relevant quotation
“There are two ways of constructing a software design: One way is to make it so simple that
there are obviously no deficiencies, and the other way is to make it so complicated that there are
no obvious deficiencies. The first method is far more difficult.”
Professor Sir Tony Hoare
1980 Turing Award Lecture; Communications of the ACM 24 (2), (February 1981): pp. 75-83
Please try to do this the first way.
Obtaining help
It is encouraged to request further clarification on what is required for this assignment. Please
try to do this during normal contact time and avoid asking for such help in the last week before
the deadline.
You can discuss the requirements and the material covered in the assignment with others but
what you create must be all your own work. Be careful to avoid collusion.
Declare in your report any help you have received other than that from the module teaching
team.
Feedback
In addition to the written feedback that we aim to provide within the normal interval, you will be
able to obtain fast, brief, verbal formative feedback and help on correcting your work at your
practical classes.
请加QQ:99515681 邮箱:99515681@qq.com WX:codinghelp
- instagram全球强力引流爆粉营销工具,ins实力推广引流营销助手
- 常州威雅夏校:预售倒计时 全能运动营超豪华运动包2024版来啦
- Ins高效筛选助手,Instagram群发代发工具,让你的营销更高效!
- 世贸通美国移民:又一批EB5投资人I-829获批,永久绿卡无忧!
- Instagram营销软件新风口,Ins自动化引流软件推荐!
- 星期零携三大产品线亮相HOTELEX上海展,覆盖植物基餐+饮场景
- 打破创意瓶颈 WhatsApp拉群工具为你的消息注入新招数
- 世贸通美国投资移民:又一批EB-5投资人心态破防了!
- 步入健康科技烹饪新时代,火星人集成灶用实力拿捏众人
- Ins引流工具,Instagram营销软件,助你实现市场吸粉领先!
- instagram低成本引流推广!Ins自动私信工具,Instagram营销软件推荐!
- 业务大爆发 博主分享 WhatsApp拉群营销工具是我海外市场制胜的法宝
- 贵州装饰网:引领装饰新风尚,缔造家居美学新境界
- 务成功博主亲述 WhatsApp拉群营销工具如何成为业务增长的法宝业
- Ins引流助手大揭秘,Instagram群发工具助你轻松拉群!
- 江西消防设备品牌:守护安全,筑牢防线
- Instagram引流营销助手,Ins拉群软件,共同助你实现营销目标!
- WhatsApp怎么养号,ws协议号购买/ws群发助手/咨询大轩
- 人生需要转折点,我在WhatsApp拉群工具的帮助下,找到了我的职业转机
- Telegram一键批量私信营销软件,每条发送上万条消息!
- 数字的盛宴 WhatsApp拉群营销工具 我的营业额节节攀升 客户询盘数暴增500%
- 数据赋能,AI创新 | 云捷亮数年会在京举办
- 创新仙方 科技魔法师的奇迹心得 WhatsApp拉群营销工具点亮商业星空
- 便捷Line代群发,助您迅速提升用户互动!
- 共话政策扶持与产业创新,东久新宜医疗器械企业闭门会成功举办
- 戴尔员工并不是唯一一个被迫减少远程工作的员工
- 创新引爆业绩 WhatsApp拉群营销工具为您的业务开创新的成功篇章
- 碧桂园服务:排查消防安全隐患、开展消防安全演练
- 新手故事 他通过WhatsApp拉群营销工具成功吸引了海量客户 业务增长率高达90%
- WD Red与追梦人|小微的天团:用极客态度向世界发声
推荐
-
 全力打造中国“创业之都”名片,第十届中国创业者大会将在郑州召开
北京创业科创科技中心主办的第十届中国创业
科技
全力打造中国“创业之都”名片,第十届中国创业者大会将在郑州召开
北京创业科创科技中心主办的第十届中国创业
科技
-
 疫情期间 这个品牌实现了疯狂扩张
记得第一次喝瑞幸,还是2017年底去北京出差的
科技
疫情期间 这个品牌实现了疯狂扩张
记得第一次喝瑞幸,还是2017年底去北京出差的
科技
-
 丰田章男称未来依然需要内燃机 已经启动电动机新项目
尽管电动车在全球范围内持续崛起,但丰田章男
科技
丰田章男称未来依然需要内燃机 已经启动电动机新项目
尽管电动车在全球范围内持续崛起,但丰田章男
科技
-
 创意驱动增长,Adobe护城河够深吗?
Adobe通过其Creative Cloud订阅捆绑包具有
科技
创意驱动增长,Adobe护城河够深吗?
Adobe通过其Creative Cloud订阅捆绑包具有
科技
-
 智慧驱动 共创未来| 东芝硬盘创新数据存储技术
为期三天的第五届中国(昆明)南亚社会公共安
科技
智慧驱动 共创未来| 东芝硬盘创新数据存储技术
为期三天的第五届中国(昆明)南亚社会公共安
科技
-
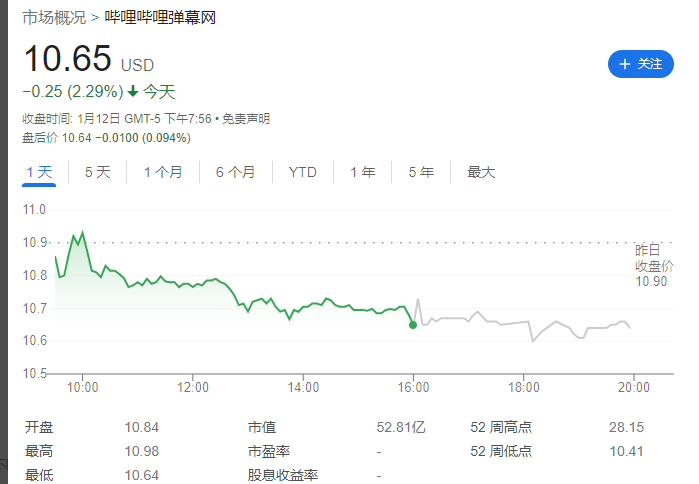 B站更新决策机构名单:共有 29 名掌权管理者,包括陈睿、徐逸、李旎、樊欣等人
1 月 15 日消息,据界面新闻,B站上周发布内部
科技
B站更新决策机构名单:共有 29 名掌权管理者,包括陈睿、徐逸、李旎、樊欣等人
1 月 15 日消息,据界面新闻,B站上周发布内部
科技
-
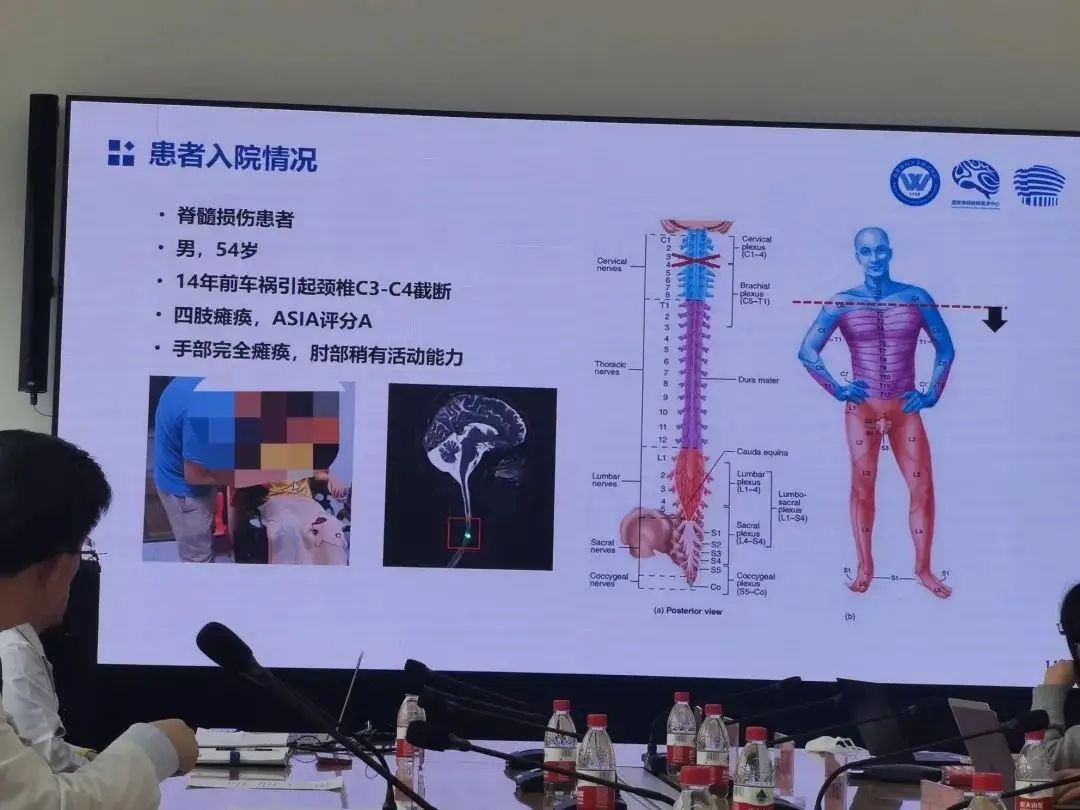 老杨第一次再度抓握住一瓶水,他由此产生了新的憧憬
瘫痪十四年后,老杨第一次再度抓握住一瓶水,他
科技
老杨第一次再度抓握住一瓶水,他由此产生了新的憧憬
瘫痪十四年后,老杨第一次再度抓握住一瓶水,他
科技
-
 升级的脉脉,正在以招聘业务铺开商业化版图
长久以来,求职信息流不对称、单向的信息传递
科技
升级的脉脉,正在以招聘业务铺开商业化版图
长久以来,求职信息流不对称、单向的信息传递
科技
-
 苹果罕见大降价,华为的压力给到了?
1、苹果官网罕见大降价冲上热搜。原因是苹
科技
苹果罕见大降价,华为的压力给到了?
1、苹果官网罕见大降价冲上热搜。原因是苹
科技
-
 如何经营一家好企业,需要具备什么要素特点
我们大多数人刚开始创办一家企业都遇到经营
科技
如何经营一家好企业,需要具备什么要素特点
我们大多数人刚开始创办一家企业都遇到经营
科技

